Amazon.com: Godiag GT105 Mini OBD2 Helper, ECU IMMO PROG, OBDII Breakout Box, Come with Free Power Cord with Battery Clip : Automotive

Amazon.com: Godiag GT105 Mini OBD2 Helper, ECU IMMO PROG, OBDII Breakout Box, Come with Free Power Cord with Battery Clip : Automotive

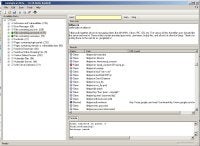
EtherGroup - #UnDíaComoHoy El hacker llamado Johnny I Hack Stuff crea Goolag Scanner. Esta aplicación es de código libre y puede ser descargada desde el sitio oficial del grupo. #Ethergroup #Hacker #goolagscanner